Unlocking The Power Of RemoteIoT Platform SSH Key For Secure Connections
Hey there, tech enthusiasts! Are you ready to dive deep into the world of remote IoT platforms and how SSH keys play a vital role in securing your connections? In today’s digital age, where IoT devices are everywhere, having a secure and reliable way to access and manage them remotely is not just important—it's essential. RemoteIoT platform SSH key acts as the digital lock and key that ensures only authorized users can access your devices. So, buckle up because we're about to explore how this technology is changing the game.
The term "remote IoT platform SSH key" might sound a bit intimidating at first, but don't worry. By the end of this article, you'll have a solid understanding of what it is, why it matters, and how you can implement it effectively. Think of it as a secret handshake between your devices and your network, ensuring that only trusted parties can join the conversation.
In the world of IoT, security is king. With cyber threats lurking around every corner, it's crucial to arm yourself with the right tools. RemoteIoT platform SSH keys are one of those tools, providing an added layer of protection that keeps your data safe and your devices secure. Now, let's get started on this exciting journey into the realm of secure IoT connections.
Read also:Mydesinet Buzz Your Ultimate Guide To The Hottest Digital Buzzword
What Exactly is a RemoteIoT Platform?
Let's start with the basics. A remote IoT platform is essentially a system that allows you to manage, monitor, and interact with IoT devices from anywhere in the world. Imagine being able to control your smart home devices, industrial sensors, or even agricultural equipment without being physically present. Sounds cool, right? But with great power comes great responsibility, and that's where SSH keys come into play.
RemoteIoT platforms offer a wide range of functionalities, including data collection, device management, and real-time monitoring. However, with all these features comes the risk of unauthorized access. That's why implementing robust security measures, like SSH keys, is crucial. These keys act as a digital passport, ensuring that only verified users can access the platform.
How Does a RemoteIoT Platform Work?
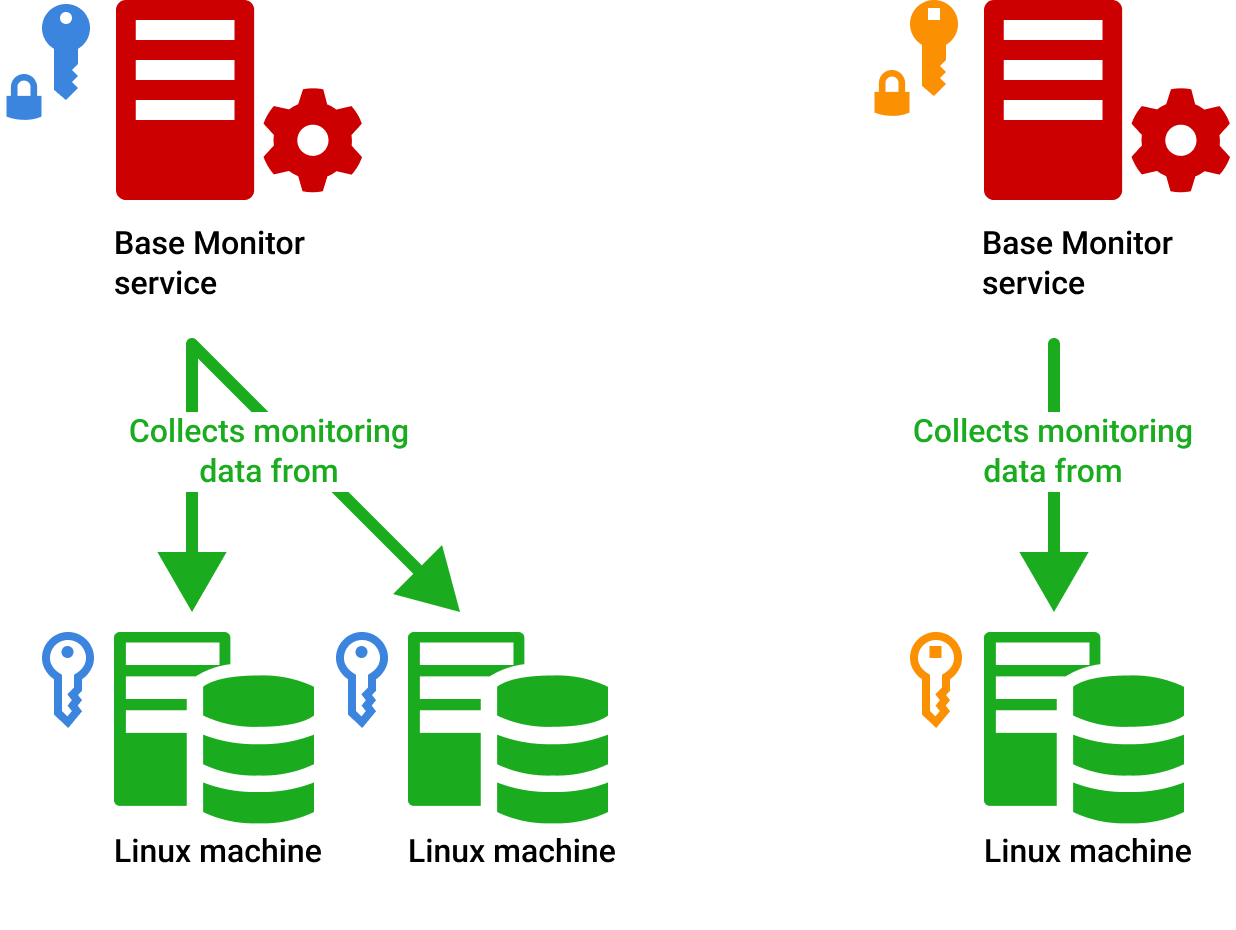
At its core, a remote IoT platform works by establishing a secure connection between your devices and a central server. This server acts as the brain of the operation, collecting data from various devices and providing insights that can be used to optimize performance. But how does it ensure that only authorized users can access this data? That's where SSH keys come in.
- Authentication: SSH keys provide a secure way to authenticate users without the need for passwords.
- Encryption: They encrypt data transmitted between devices and the server, ensuring that even if someone intercepts the data, they won't be able to read it.
- Access Control: SSH keys allow administrators to control who has access to specific devices or parts of the platform.
The Role of SSH Keys in RemoteIoT Platforms
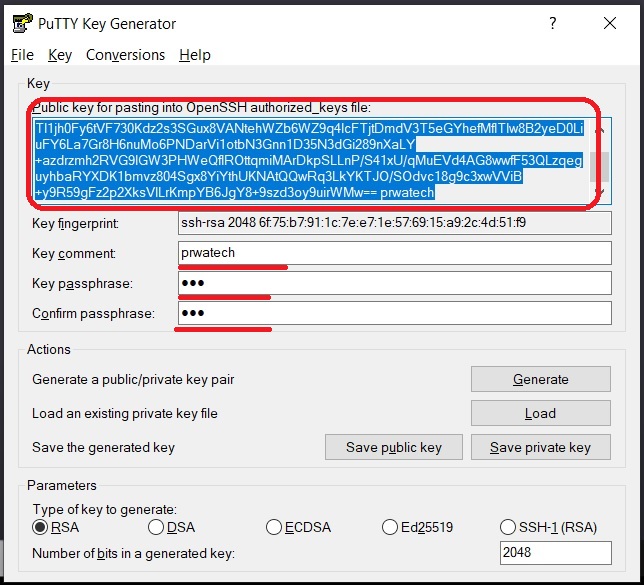
Now that we understand what a remote IoT platform is, let's talk about the star of the show: SSH keys. SSH stands for Secure Shell, and it's a protocol used to securely access remote computers or devices. SSH keys are a pair of cryptographic keys—one public and one private—that are used to authenticate users and encrypt data.
When it comes to remote IoT platforms, SSH keys are essential for maintaining security. They ensure that only authorized users can access the platform and its devices, preventing unauthorized access and potential data breaches. In a world where cyber threats are becoming increasingly sophisticated, SSH keys provide an extra layer of protection that can't be ignored.
Why Use SSH Keys Over Passwords?
You might be wondering why SSH keys are preferred over traditional passwords. Well, here are a few reasons:
Read also:Jasmine Sherni The Rising Star Whos Captivating The World
- Increased Security: SSH keys are much harder to crack than passwords, making them a more secure option.
- No Password Management: With SSH keys, you don't have to worry about remembering complex passwords or resetting them regularly.
- Two-Factor Authentication: SSH keys can be used as part of a two-factor authentication process, adding an extra layer of security.
Setting Up SSH Keys for Your RemoteIoT Platform
Setting up SSH keys for your remote IoT platform might sound complicated, but with the right guidance, it's actually quite straightforward. Here's a step-by-step guide to help you get started:
- Generate SSH Key Pair: Use a tool like SSH-Keygen to generate a public and private key pair.
- Copy Public Key to Server: Copy the public key to the server where your remote IoT platform is hosted.
- Configure SSH Settings: Update your SSH settings to disable password authentication and require SSH keys for access.
- Test Connection: Try connecting to your server using the SSH key to ensure everything is set up correctly.
Best Practices for Managing SSH Keys
Once you've set up SSH keys for your remote IoT platform, it's important to follow best practices to ensure they remain secure. Here are a few tips:
- Limit Access: Only grant SSH key access to trusted users.
- Regularly Rotate Keys: Periodically update your SSH keys to prevent unauthorized access.
- Store Keys Securely: Keep your private key in a secure location and never share it with anyone.
Benefits of Using SSH Keys in RemoteIoT Platforms
Now that we've covered the basics of setting up SSH keys, let's talk about the benefits they bring to remote IoT platforms. Here are a few key advantages:
- Enhanced Security: SSH keys provide a more secure method of authentication than passwords.
- Improved Efficiency: With SSH keys, you don't have to worry about remembering complex passwords, saving you time and hassle.
- Scalability: SSH keys can be easily scaled to accommodate growing networks of IoT devices.
Real-World Applications of SSH Keys in IoT
SSH keys are not just theoretical concepts; they have real-world applications in various industries. For example:
- Smart Cities: SSH keys are used to secure communication between smart city infrastructure and central management systems.
- Healthcare: In the healthcare industry, SSH keys ensure that sensitive patient data is transmitted securely between devices and servers.
- Manufacturing: Manufacturers use SSH keys to secure communication between industrial IoT devices and control systems.
Common Challenges and Solutions
While SSH keys offer many benefits, there are also some challenges that come with implementing them. Here are a few common issues and how to address them:
- Key Management: Managing a large number of SSH keys can be challenging. Use a key management system to keep track of all your keys.
- Key Rotation: Regularly rotating SSH keys can be time-consuming. Automate the process using scripts or tools.
- Access Control: Ensuring that only authorized users have access to SSH keys can be difficult. Implement strict access control policies.
Tips for Troubleshooting SSH Key Issues
Encountering issues with SSH keys is not uncommon, but don't worry. Here are a few tips to help you troubleshoot:
- Check Permissions: Make sure the permissions on your SSH key files are set correctly.
- Verify Key Format: Ensure that your SSH keys are in the correct format and haven't been corrupted.
- Test Connectivity: Try connecting to your server using a different client to rule out client-side issues.
Future Trends in RemoteIoT Platforms and SSH Keys
The future of remote IoT platforms and SSH keys looks bright. As technology continues to evolve, we can expect to see even more advanced security features and easier-to-use tools. Here are a few trends to watch out for:
- Quantum-Resistant Cryptography: As quantum computing becomes more prevalent, new cryptographic methods will be developed to ensure SSH keys remain secure.
- AI-Driven Security: Artificial intelligence will play a bigger role in detecting and preventing unauthorized access to IoT platforms.
- Blockchain Integration: Blockchain technology could be used to enhance the security and transparency of SSH key management.
Preparing for the Future
To prepare for the future of remote IoT platforms and SSH keys, it's important to stay informed about the latest trends and technologies. Continuously educate yourself and your team about best practices and emerging threats. By doing so, you'll be able to adapt quickly to changes and ensure the security of your IoT infrastructure.
Conclusion
And there you have it—a comprehensive guide to understanding and implementing SSH keys in remote IoT platforms. From enhancing security to improving efficiency, SSH keys offer numerous benefits that make them an essential tool for anyone working with IoT devices. Remember, security is not a one-time task; it's an ongoing process that requires vigilance and adaptability.
So, what are you waiting for? Start exploring the world of remote IoT platforms and SSH keys today. And don't forget to share your thoughts and experiences in the comments below. Together, we can build a safer and more connected future!
Table of Contents
Article Recommendations