Unlocking The Power Of RemoteIoT Platform SSH Key: Your Ultimate Guide
Alright folks, let’s dive straight into the world of cutting-edge technology and remote management. If you’ve ever wondered how to secure your IoT devices while managing them remotely, you’re in the right place. RemoteIoT platform SSH key is the game-changer you’ve been waiting for. This isn’t just another tech buzzword; it’s a solution that combines security, efficiency, and flexibility. So, buckle up, because we’re about to break it down in a way that even your grandma could understand—well, almost.
In today’s hyper-connected world, securing your devices is no longer optional. Whether you’re managing a smart home, an industrial automation system, or even a fleet of drones, the RemoteIoT platform SSH key is your secret weapon. It’s like having a digital bouncer at the door of your IoT network, ensuring only the right people—or rather, the right keys—get access. This guide will walk you through everything you need to know, from the basics to advanced tips, so you can make the most out of this powerful tool.
Before we dive deeper, let’s set the stage. Think of the RemoteIoT platform as your digital command center. It’s where all your IoT devices communicate, share data, and receive instructions. But here’s the thing: without proper security measures, this command center becomes vulnerable to hackers and cyber threats. That’s where SSH keys come in. They act as a digital lock and key system, ensuring that only authorized users can access your devices. Ready to learn more? Let’s go!
Read also:Mia Khalifa With Her Boyfriend The Untold Story Youve Been Waiting For
What Exactly is a RemoteIoT Platform SSH Key?
Let’s get technical for a moment, but don’t worry, we’ll keep it simple. An SSH key is essentially a pair of cryptographic keys used to authenticate users and devices in a secure manner. In the context of the RemoteIoT platform, these keys play a crucial role in establishing a secure connection between your devices and the platform. It’s like having a secret handshake that only you and your trusted devices know.
Here’s the kicker: SSH keys are far more secure than traditional passwords. Why? Because they use complex algorithms that are nearly impossible to crack. Plus, they eliminate the need to remember long, complicated passwords, which let’s face it, most of us struggle with anyway. By using SSH keys, you’re not just securing your devices; you’re simplifying your life.
Why Use SSH Keys Over Passwords?
Now, you might be wondering, “Why bother with SSH keys when passwords have worked fine so far?” Well, here’s the deal: passwords are outdated. They’re prone to brute-force attacks, phishing scams, and let’s not forget, the human tendency to use weak or reused passwords. SSH keys, on the other hand, offer several advantages:
- Enhanced Security: SSH keys are far more secure than passwords, making it nearly impossible for hackers to gain unauthorized access.
- No Password Hassle: Say goodbye to remembering complex passwords. Once you set up your SSH keys, you’re good to go.
- Automation Friendly: SSH keys are perfect for automated processes, allowing seamless communication between devices without manual intervention.
So, if you’re still relying on passwords to secure your IoT devices, it’s time to upgrade. Trust us, your future self will thank you.
How Does RemoteIoT Platform SSH Key Work?
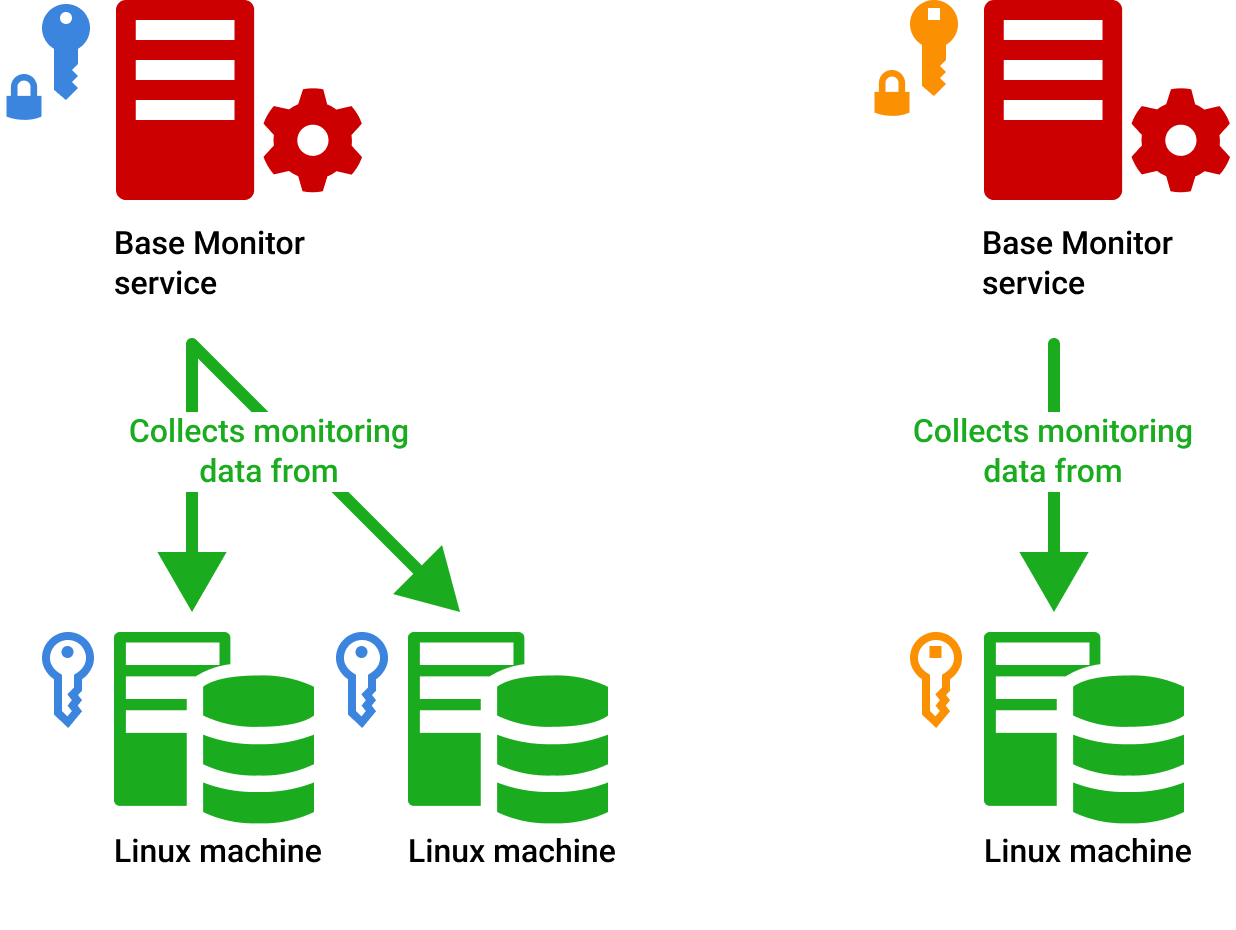
Alright, let’s break it down step by step. When you set up an SSH key on the RemoteIoT platform, you’re essentially creating a public-private key pair. The public key is shared with the platform, while the private key stays securely on your device. Think of it like a mailbox: anyone can drop a letter in (the public key), but only you have the key to open it (the private key).
Here’s how the process works:
Read also:Indian Mms World The Ultimate Guide To Understanding Its Impact And Significance
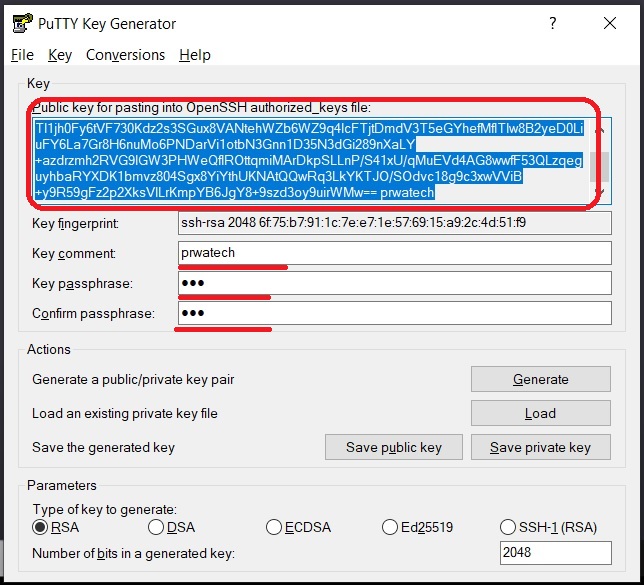
- Key Generation: First, you generate a pair of SSH keys using a tool like OpenSSH or PuTTYgen.
- Public Key Sharing: Next, you upload the public key to the RemoteIoT platform. This tells the platform that you’re authorized to access its resources.
- Secure Connection: When you attempt to connect to the platform, it verifies your identity by checking the private key on your device against the public key it has on file. If they match, you’re granted access.
It’s like a digital handshake that happens in the background, ensuring that only trusted devices can communicate with each other. Pretty cool, right?
Setting Up SSH Keys on RemoteIoT Platform
Now that you understand how SSH keys work, let’s talk about setting them up. Don’t worry; it’s easier than it sounds. Here’s a step-by-step guide to help you get started:
- Generate SSH Keys: Use a tool like OpenSSH to generate your key pair. Make sure to save both the public and private keys in a secure location.
- Upload Public Key: Log in to your RemoteIoT platform account and navigate to the settings section. Look for the option to upload your public SSH key and follow the prompts.
- Test the Connection: Once your keys are set up, try connecting to the platform to ensure everything is working as expected. If you run into any issues, double-check your key settings and try again.
And just like that, you’re all set. With SSH keys in place, your RemoteIoT platform is now more secure and efficient than ever.
The Importance of Secure IoT Management
In today’s digital landscape, IoT security is more important than ever. With billions of devices connected to the internet, the risk of cyber attacks is higher than ever before. That’s why platforms like RemoteIoT and tools like SSH keys are essential for maintaining the integrity and security of your network.
Think about it: every device you connect to the internet is a potential entry point for hackers. Without proper security measures, your smart home, business operations, or even critical infrastructure could be at risk. But with SSH keys, you’re adding an extra layer of protection that makes it exponentially harder for attackers to gain access.
Common IoT Security Threats
Before we move on, let’s quickly touch on some of the most common IoT security threats:
- Brute-Force Attacks: Hackers use automated tools to guess passwords until they find the right one. SSH keys eliminate this risk by removing the need for passwords altogether.
- Man-in-the-Middle Attacks: Attackers intercept communication between devices to steal sensitive data. SSH keys encrypt all communication, making it nearly impossible for attackers to eavesdrop.
- Firmware Vulnerabilities: Outdated or poorly secured firmware can leave devices vulnerable to attacks. Regularly updating your devices and using SSH keys can help mitigate this risk.
By understanding these threats and taking proactive measures, you can protect your IoT network from potential disasters.
Benefits of Using RemoteIoT Platform SSH Key
Now that we’ve covered the basics, let’s talk about the benefits of using SSH keys with the RemoteIoT platform. Here’s what you stand to gain:
- Improved Security: SSH keys provide a higher level of security than traditional passwords, protecting your devices from unauthorized access.
- Increased Efficiency: With SSH keys, you can automate tasks and streamline processes, saving you time and effort.
- Enhanced Scalability: As your IoT network grows, SSH keys make it easier to manage multiple devices and users without compromising security.
These benefits aren’t just theoretical; they’re backed by real-world data. Studies have shown that organizations using SSH keys for IoT management experience fewer security breaches and higher operational efficiency. So, if you’re looking to take your IoT setup to the next level, SSH keys are the way to go.
Real-World Examples of SSH Key Implementation
To give you a better idea of how SSH keys work in practice, let’s look at a couple of real-world examples:
- Smart Home Automation: A homeowner uses SSH keys to securely manage their smart home devices, ensuring that only authorized users can access their network.
- Industrial IoT: A manufacturing company uses SSH keys to secure communication between machines on the factory floor, reducing downtime and increasing productivity.
These examples illustrate the versatility and effectiveness of SSH keys in various applications. Whether you’re managing a small home network or a large-scale industrial operation, SSH keys can help you achieve your goals.
Best Practices for Managing SSH Keys
Now that you know the benefits of SSH keys, let’s talk about how to manage them effectively. Here are some best practices to keep in mind:
- Store Keys Securely: Keep your private SSH key in a secure location, such as an encrypted folder or hardware security module (HSM).
- Regularly Rotate Keys: Just like passwords, SSH keys should be rotated periodically to minimize the risk of compromise.
- Limit Access: Only grant SSH key access to trusted users and devices, and regularly review your access lists to ensure they’re up to date.
By following these best practices, you can maximize the security and effectiveness of your SSH keys.
Common Mistakes to Avoid
While SSH keys are a powerful tool, they’re not foolproof. Here are some common mistakes to avoid:
- Leaving Keys Unprotected: Storing your private key in an unencrypted file or sharing it with others can compromise your security.
- Using Weak Keys: Generating keys with weak algorithms or short lengths can make them more vulnerable to attacks.
- Not Rotating Keys: Failing to rotate your keys regularly can leave your network exposed to potential threats.
By avoiding these mistakes, you can ensure that your SSH keys remain a strong line of defense for your IoT network.
Future Trends in IoT Security
As technology continues to evolve, so do the threats facing IoT networks. That’s why it’s important to stay informed about the latest trends and advancements in IoT security. Here are a few to keep an eye on:
- Quantum Computing: While still in its infancy, quantum computing has the potential to break traditional encryption methods, making it essential to develop quantum-resistant algorithms.
- AI-Powered Security: Artificial intelligence is being used to detect and respond to threats in real-time, providing an extra layer of protection for IoT networks.
- Blockchain Technology: Blockchain is being explored as a way to enhance IoT security by providing a decentralized and tamper-proof ledger for device communication.
By staying ahead of these trends, you can ensure that your IoT network remains secure and efficient in the years to come.
Preparing for the Future
So, how do you prepare for the future of IoT security? Start by educating yourself and your team about the latest threats and technologies. Invest in tools like SSH keys and other security measures to protect your network. And most importantly, stay vigilant and proactive in your approach to security.
Conclusion: Take Control of Your IoT Security Today
Alright folks, that’s a wrap. We’ve covered a lot of ground today, from the basics of SSH keys to the future of IoT security. By now, you should have a solid understanding of how RemoteIoT platform SSH keys can help you secure your IoT network and streamline your operations.
So, what’s next? We encourage you to take action. Generate your SSH keys, set them up on your RemoteIoT platform, and start enjoying the benefits of enhanced security and efficiency. And don’t forget to share this article with your friends and colleagues who could benefit from this knowledge.
Remember, in the world of IoT, security isn’t just an option—it’s a necessity. With SSH keys and the RemoteIoT platform, you have the tools you need to protect your network and stay ahead of the curve. So, what are you waiting for? Get started today!
Table of Contents
Article Recommendations